February 1 – 2, 2024

NSF TRIPODS Workship
The NSF TRIPODS Workshop brings together a large and diverse team of researchers from each of the TRIPODS centers: EnCORE, FODSI, IDEAL, and IFDS. The aim of the Transdisciplinary Research In Principles Of Data Science (TRIPODS) is to connect the statistics, mathematics, and theoretical computer science communities to develop the theoretical foundations of data science through integrated research and training activities focused on core algorithmic, mathematical, and statistical principles. This workshop focuses on the contributions of each center’s work.
- Thursday, February 1, 2024 to Friday, February 2, 2024
- Room 1242 in the CSE Building at UC San Diego and Zoom
- Registration Link
Agenda
- Thursday, February 1
- Friday, February 2
08:00 AM - 09:15 AM Registration & Breakfast
09:15 AM - 09:30 AM Welcome & Opening Remarks
- Barna Saha, Director of EnCORE, UC San Diego
09:30 AM - 10:30 AM Plenary Talk
- Emmanuel Candes, Barnum-Simons Chair in Mathematics and Statistics, Stanford
University
10:30 AM - 12:00 PM TRIPODS Institute Talks
- FODSI - Piotr Indyk (MIT)
- IFDS - Rob Nowak (Wisc)
- IDEAL - Matt Walter (TTIC)
- EnCORE - Sanjoy Dasgupta (UCSD)
12:00 PM - 1:30 PM Lunch On Your Own
- The Price Center offers many options. A map to Price Center and various options can be found in the "Lunch On Your Own" section on this page. (Directions can be found here. It is an estimated 5-minute walk).
1:30 PM - 2:30 PM Panel Session: Role of Foundations in Data Science
- Moderator: Raghu Meka (UCLA)
- Emmanuel Candes (Stanford)
- Piotr Indyk (MIT)
- Arya Mazumdar (UCSD)
- Rob Nowak (U Wisconsin)
- Nati Srebro (TTIC)
2:30 PM - 4:00 PM Lightning Talks
- Hadley Black
- Neophytos Charalambides
- Eric Evert
- Charlie Guan
- Nirmit Joshi
- Gene Li
- Marko Medvedev
- Ronak Mehta
- Shyam Narayanan
- Max Ovsiankin
- Kumar Kshitij Patel
- Kavya Ravichandran
- Sandeep Silwal
- Jake Soloff
- Vaidehi Srinivas
- Arsen Vasilyan
- Zhengchao Wan
4:00 PM - 5:30 PM Poster Session / Snack Break (Lobby)
- Hadley Black
- Neophytos Charalambides
- Eric Evert
- Charlie Guan
- Nirmit Joshi
- Gene Li
- Marko Medvedev
- Ronak Mehta
- Shyam Narayanan
- Max Ovsiankin
- Kumar Kshitij Patel
- Kavya Ravichandran
- Sandeep Silwal
- Jake Soloff
- Vaidehi Srinivas
- Arsen Vasilyan
- Zhengchao Wan
6:00 PM - 8:00 PM Faculty Dinner (Faculty Only)
- Puesto La Jolla - 1026 Wall Street, La Jolla, CA 92037 (Estimated 15-20 drive/rideshare).
08:00 AM - 09:00 AM Registration & Breakfast
09:00 AM - 10:00 AM Industry Plenary Talks
- Sanjiv Kumar, VP, Google Research
- S. Muthukrishnan, VP, Sponsor Products, Amazon Ads
10:00 AM - 10:30 AM Break
10:30 AM - 11:30 AM Panel Session: Mentoring Panel for Students: How to be Successful in Your Career
- Moderator: Arya Mazumdar (UCSD)
- Samir Khuller (NU)
- Raghu Meka (UCLA)
- Sujay Sanghavi (UT Austin)
- Rajiv Gandhi (Rutgers Camden & UPenn)
11:30 AM - 01:00 PM Lunch On Your Own
- The Price Center offers many options. A map to Price Center and various options can be found in the "Lunch On Your Own" section on this page. (Directions can be found here. It is an estimated 5-minute walk).
01:00 PM - 02:30 PM TRIPODS Institute Talks
- EnCORE - Sujay Sanghavi (UT)
- IDEAL - Aravindan Vijayaraghavan (NU)
- IFDS - Zaid Harchaoui (U Washington)
- FODSI - Sandeep Silwal (MIT)
02:30 PM - 03:00 PM Snack Break
03:00 PM - 04:00 PM Panel Session: AI vs. Data Science vs. Computer Science: How to Remain Research-Relevant
- Moderator: Sujay Sanghavi (UT Austin)
- Enis Cetin (UIC)
- Sorin Lerner (UCSD)
- Piotr Indyk (MIT)
- Rose Yu (UCSD)
- Rajesh Gupta (UCSD)
Lunch On Your Own
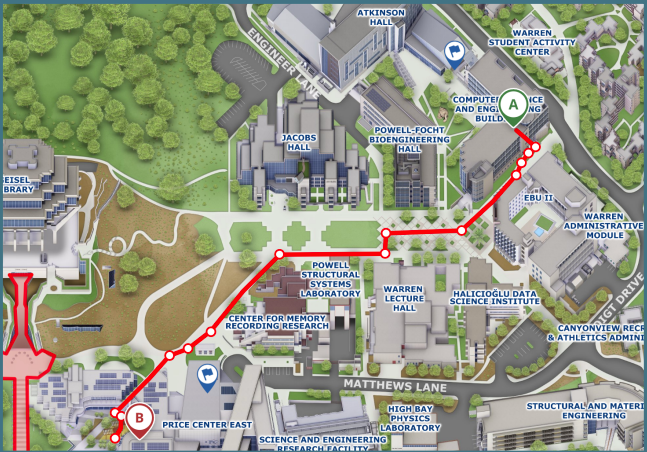
Price Center is an estimated 5-minute walk from the Computer Science and Engineering (CSE) Building. A map displaying the route from the CSE Building to Price Center can be seen on the left.
There are a variety of different food options available at the UCSD Campus, including Price Center. Price Center is an estimated 5-minute walk from the Computer Science and Engineering (CSE) Building. A map displaying the route from the CSE Building to Price Center can be seen on the left. Directions can also be found here.
Alternative dining options on campus can be found here.
The Price Center offers many options, including the following:
Burger King
Curry Up Now
Dirty Birds
Jamba Juice
Lemongrass
Panda Express
Rubio’s Costal Grill
Santorini Greek Island Grill
Seed + Sprout
Starbucks
Subway
Sunshine Market
Tapioca Express
Zanzibar Cafe at The Loft
Event Pictures